Let’s say you make the wise decision to ensure continuous uptime for your network by leveraging multiple WAN links from different ISPs and you have configured them for automatic failover using an intelligent WAN appliance. If one link fails, your traffic will automatically switch to the other links.
…But what happens if the failover device fails?
The prudent thing to do is install a redundant device for hardware failover, also known as High Availability or HA pair. You can also use the device’s network bypass function to keep traffic flowing until you can fix the problem or replace the device.
This feature is known by many names: fail-to-wire, FTW, LAN bypass, network bypass, LAN failsafe, take your pick. It’s a fault-tolerance feature of networking hardware that protects essential business communications in the event of a power outage and/or system failure. It allows traffic to pass through while the appliance is shut down, rebooting, or has unexpectedly lost power.
How Network Bypass Works
LAN ports are bridged together in pairs through mechanical relays. If the network appliance loses power, data traffic between the paired LAN ports can still continue and network uptime is unaffected.
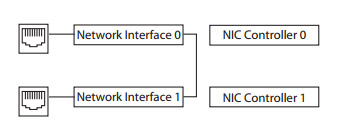
Figure 1: Bypass status
Ethernet network ports are disconnected from the system interfaces. A crossed connection loop-back between the Ethernet ports is established.
The native features of the device won’t be available during this mode of operation. For example, if the hardware offers content filtering, load balancing, packet duplication, etc, that will not be operational. As the name implies, fail to wire simply provides a raw connection so that traffic can continue to pass through for the sake of business continuity.
Network bypass has evolved since its inception. In this article, we’ll look at three iterations of network bypass.
Generation One Bypass
In its earliest stages, the bypass function was controlled by a hardware jumper on the appliance’s main board. When the jumper connected the two pins on the jumper block, bypass would be enabled when the system was powered off. If a system shut down, communication could still carry on. This is referred to as a system-off bypass. If the system was powered on, and the jumper was set to enable bypass, software could be used to switch bypass on or off as required. But bypass was always enabled when the system was turned off, even if software had been used to disable bypass. Also, the pairs could not be independently controlled; the same setting was applied to all bypass pairs.
Generation Two Bypass
In Generation Two, the hardware jumper was no longer necessary. Generation Two featured a new design using a combination of latch relays and software. In this program, the system administrator could set the bypass to be enabled or disabled if the system shut down, and the relays would link the ports of bypass pairs. With no hardware jumpers required, these settings could also be changed remotely. Another benefit in Generation Two was that the settings could be different for different bypass pairs. One pair could have bypass enabled when the system shut down and another pair could have bypass disabled.
For both the first and the second generation of bypass, it was possible to use a watchdog timer (shared between the bypass and the system) to enable bypass if the system had a glitch and hung. Some instances remained, however, where packet loss could occur for a fraction of a millisecond while the system was just powering on. For some extremely sensitive or mission critical applications, this is not desireable. Streaming technologies, voice over IP, online gaming and videoconferencing demand timely delivery of sequential packets. Lost or dropped packets can result in highly noticeable performance issues. In the transmission of text files, a single packet loss could result in file corruption.
Generation Three Bypass
Generation Three solved the lost or dropped packet issue by enabling lossless packet transfers at the start of the system just-on state. This form of bypass uses a microcontroller for more flexibility and more advanced functionality. Complex configurations can be stored in the microcontroller’s non-volatile memory, regardless of the system’s operating state.
Now each pair of bypass ports has their own watchdog timer, which frees the system watchdog timer to handle automatic resets or other corrective actions. Generation Three runtime watchdog timers help software to detect abnormal system behavior, which can then be used to trigger the bypass function. A programmable timer switch handles the bypass during the first few seconds when a system is turned on. This is a useful function for systems where an automatic reset by a watchdog timer has occurred and bypass status needs to be controlled at all times.
Generation Three Bypass features:
- Communication through SMBus (I2C).
- Independent bypass status control for each pair of ports, up to a total of four pairs.
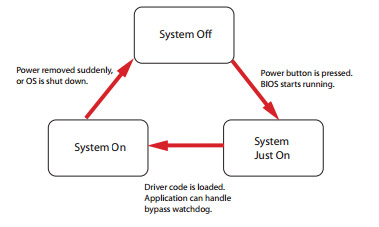
- Ability to bypass Ethernet ports on a host system in response to three instances (see figure 2):
- System off
- Just-on (just-on is the brief moment when the internal power supply turns on and booting process is in progress)
- System on (software request during runtime).
- Reset of system during runtime if system hangs without packet loss.
- Software programmable bypass or normal status.
- Software programmable timer interval for just-on moment.
Summary
Depending on your network architecture and the advanced applications your organization deploys, you may find you need to enable and disable bypass no matter if the system is on, off, or in the process of restarting. Generation Three bypass offers a very high level of LAN bypass control. Even if the system unexpectedly shuts down, Generation Three enables the LAN bypass to be managed with greater accuracy and reliability, maximizing network uptime. In addition, Generation Three adds dedicated watchdogs for different pairs of bypass ports during runtime. This is an important advantage when your network device serve multiple connections for multiple network sites.
Knowing what generation of bypass your WAN devices support can help you architect the most reliable and responsive network to meet your organization’s needs.
If you would like to speak with one of Ecessa’s engineers about fail-to-wire or any other WAN topic, please call us toll free at 1.800.669.6242 or fill out the contact form below. We love helping networking professionals succeed.
Share this article!