Resiliency and security are the top concerns for every business, large and small. A day does not go by without reports of another ransomware attack. Companies must be proactive in upgrading, testing and reinforcing their security infrastructure and incidence avoidance and response activities. According to Small Business Trends, 43 percent of cyber-attacks target small business, and 60 percent of small companies go out of business within six months of being attacked. In addition, with millions of workers now accessing corporate networks remotely, hackers have even more opportunities to compromise systems, implant malware and disrupt not only individual businesses, but entire economic sectors. Enhanced cybersecurity is a must, and any network infrastructure changes you make must have security features, capabilities and a track record of success. Ecessa SD-WAN provides multiple layers of security to enhance and improve your existing security strategy.
Security with Ecessa’s Integrated Firewall
Every Ecessa product comes with a Layer 7 Next Generation Firewall that blocks threats to your network and your users. Ecessa can be your primary firewall, add a layer of security to your network edge, or simply play nicely with the enterprise firewall you already have in place. With that flexibility, you can decide what is best for your business.
One Ecessa customer, who had switched to dual-WAN firewalls, recently replaced them with new Ecessa units. His reason? “We missed the reliability, ease of use and configuration and great support of Ecessa.”

Ecessa firewall features include:
- Intrusion Detection and Prevention (IDS/IPS) with Anti-malware/Anti-virus protection
- Selectable threat classes (Malware, Ransomware, DDoS)
- Threat package updates (automatic and configurable)
- Geoblocking of traffic based on geography
- Website filtering
- Custom rules engine
- SSL VPN authentication using username and password
- SSL VPN multi-factor authentication (MFA) using Duo
- Customizable inbound and outbound rules
- Quality of Service (QoS) engine
- Access Control List (ACL) with change logs
- Full read/write control of all rules and policies
- Full reporting, logging and alerting
Encryption with SD-WAN
Ecessa SD-WAN also provides industry standard encryption engines that you know and rely on today, such as 128- and 256-bit IPsec or SSL VPNs. Ecessa can interoperate with your existing infrastructure; we are able to natively create and manage VPNs for your remote locations or users regardless of the connection type or provider. Ecessa also offers the ability to selectively encrypt your SD-WAN tunnels, providing more tools for you to customize the solution to meet the unique needs of your business. This flexibility helps secure public broadband connections and augment your existing network security with as little disruption as possible.
Multilayered Cyber Protection
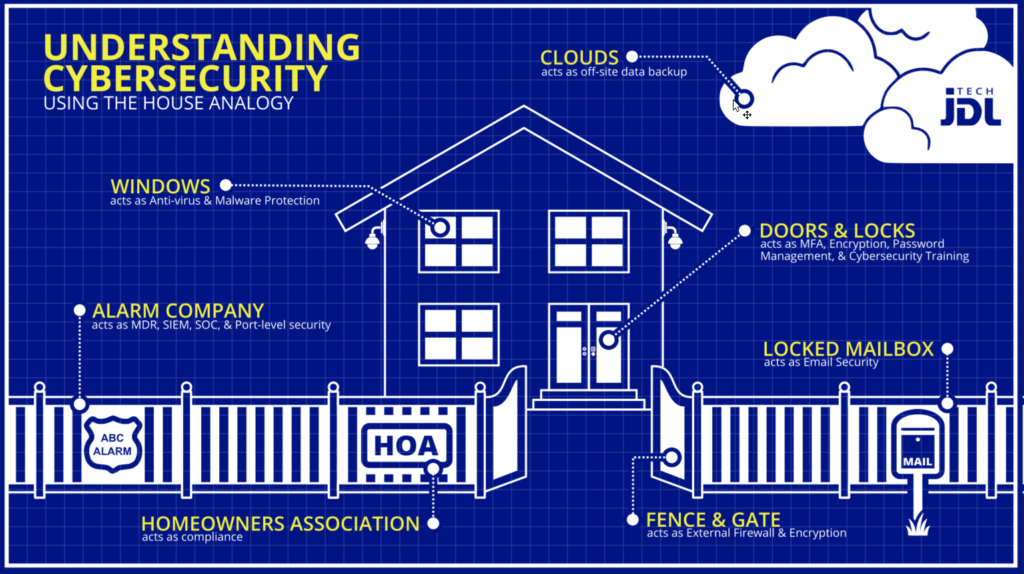
Advanced firewalls and encryption aren’t the only cyber hygiene measures you need to protect against intrusion and criminal threats. A multilayered cybersecurity solution includes multi-factor authentication, anti-virus and anti-malware software, email filtering, complete endpoint security and security awareness training for everyone in your organization. OneNet Global can install and manage comprehensive cyber protection for your business.
Solution: WANworX
WANworX® Secure SD-WAN combines reliable hardware, innovative software, network design,
and support services to allow organizations to operate from multiple locations seamlessly.
SD-WAN SECURITY FOR
REGULATED INDUSTRIES
Regulated industries, like banking or healthcare, must adhere to strict security guidelines in order to protect critical and sensitive data, often leveraging private connections and extra layers of encryption to secure communications, transactions, or data replication for disaster recovery requirements. When Stearns Bank needed additional bandwidth to support high-speed access and superior security measures, they worked with Ecessa and other partners to craft a technology solution that ensured safeguards and satisfied the banking industry’s high standard for security and compliance. The Ecessa team helped determine why Stearns Bank wasn’t getting the speed they needed while providing additional bandwidth and security along the way.
View the Case Study
