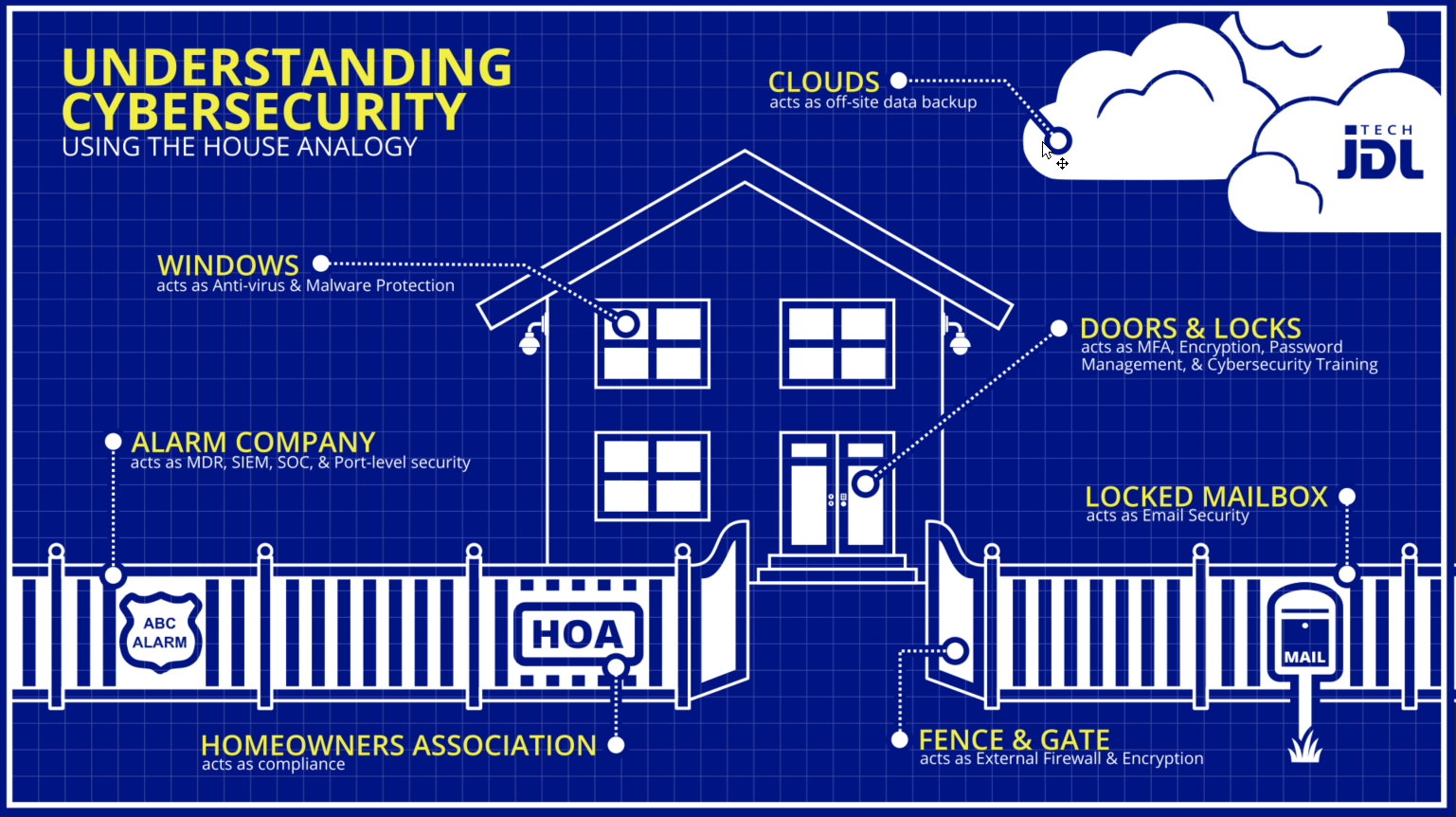
Just as you likely have several layers of physical security protecting your home, every organization should implement multiple layers of cybersecurity. In this article, developed by the unified IT teams of JDL Technologies and Ecessa, we will show you how different forms of cybersecurity technology work together to form a strong shield against unwanted intrusion, data theft and exploitation by criminals.
Fence & Gate
A firewall acts as your fence and gate, your first line of defense. A VPN makes it possible to securely access applications and resources remotely that would otherwise be inaccessible from offsite locations, while also encrypting connections and providing some access control for corporate networks.
Locked Mailbox
Email content control and data leak prevention (DLP) scans subject, body, and attachments to detect, encrypt, or block the sending or receiving of sensitive information.
Door Locks
Multi-factor authentication (MFA) is a security enhancement that uses multiple barriers to entry to prevent hackers from gaining access to personal information and sensitive corporate data. Encryption protects digital data stored on computer systems and as it is transmitted using the internet or privately to other computer networks. Password management keeps login and password credentials private. Security awareness training equips everyone in an organization with the information they need to protect themselves and their organization’s assets from loss or harm.
Windows
Anti-virus and malware prevention utilities handle Trojans, rootkits, spyware, adware, ransomware, and more.
Clouds
Off-site data backup is essential in today’s world of ransomware attacks to help recover stolen data, continue working and prevent further revenue loss.
Alarm Company
MDR, SIEM, SOC, and port-level security features monitor activity on a network. When unauthorized activity is detected, protections can automatically be invoked and IT teams notified.
HOA
Compliance mandated by government agencies and industry groups provides incentives (like avoiding fines and other punishments) for proving the use of cybersecurity best practices.
As we’ve seen in recent years, even the largest organizations in the world with presumably excellent cybersecurity practices can find their networks compromised. Having a crisis management plan documented is highly advised. Buying ransomware insurance for your organization may also be worth looking into (and then making sure you have all the preventative measures in place that the insurer requires). And if your organization doesn’t have a Chief Information Officer (CIO) or Chief Information Security Officer (CISO), Ecessa/JDL Technologies can supply the expert help you need with our virtual CIO and vCISO services.
Contact us today to learn more about adding multilayered cybersecurity to protect your organization.
